RISK INTELLIGENCE
Do you know everything stored on your organization’s network and the risk associated with the stored data?
Storing some types of data comes with a higher liability and can also cause you to fail PCI compliance. Cyber liability policies are starting to check on the liability of data stored on your systems now more than ever and can even deny your company coverage.
Risk Intelligence enables JTC to quickly and easily perform ongoing risk and vulnerability assessments of Windows computers, calculating real-time risk of a data breach and assigning a monetary value. This process is achieved through scans on all servers and client systems on the network.
With Risk Intelligence, it’s possible to:
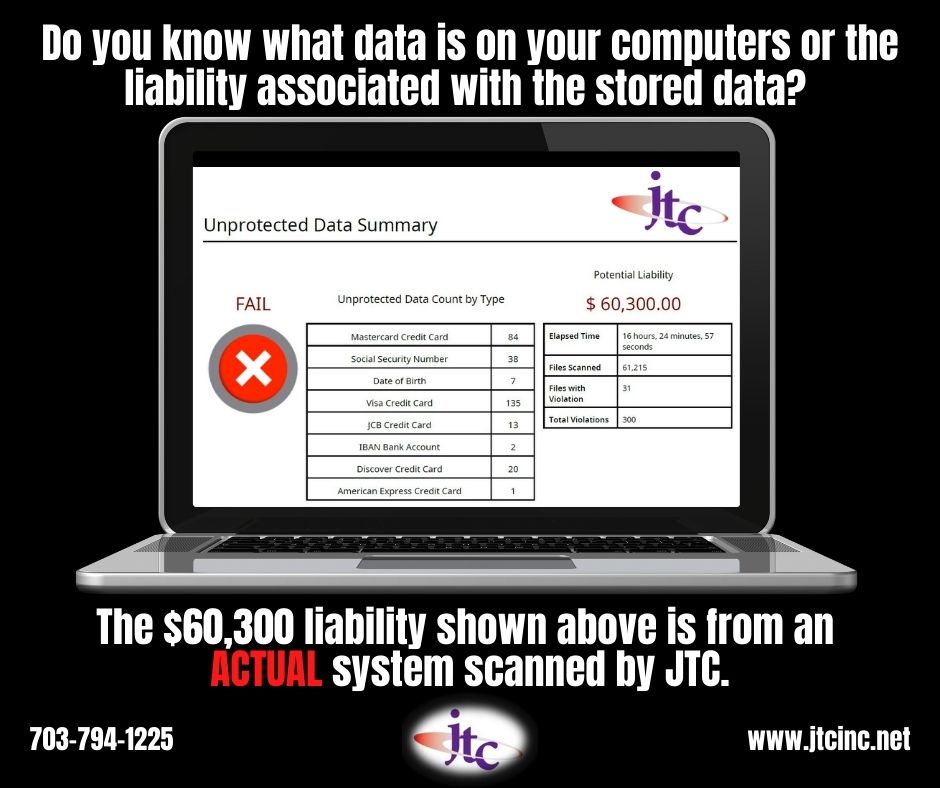
- Gain visibility of any sensitive data on the device: easily identify unprotected data and its location – including highly-sensitive Personally Identifiable Information (PII) such as Credit Card Numbers, dates of birth, government-issued identification, and financial account numbers – to understand how an attacker would compromise it, and how much a data breach would cost.
- Minimize the risk of a data breach: avoid cost-prohibitive and crippling data breaches; which can be detrimental not only to the business itself but also to its reputation.
- Build a business case for security projects: understand the total risk exposure within the IT environment in monetary terms and use this insight to connect security to business value; to help justify the resources and expenditure required to better safeguard data.
- Demonstrate regulatory compliance: satisfy a host of highly punitive compliance requirements that mandate periodic risk assessments and audits, including HIPAA, PCI DSS, and FINRA.
- Offer more holistic security: adopt a data-centric approach to security that addresses unprotected data, regardless of where it lives.
Once the initial scan is performed, JTC will provide you with a report showing the risk and assist in clearing up the potential liability. Once the liability is assessed, scans can be run weekly or monthly to ensure your data remains risk free





